There are over 70 body parts– each with a unique size and shape – that contribute to how a person speaks. Voice biometrics relies on the fact that human voice characteristics correlate strongly to the physiological qualities of how a person creates speech. Unlike other methods of authentication, voice biometrics does not rely on a secret such as the person remembering a passphrase. It isn’t what the person says that is being authenticated, it’s who is speaking.
More than 70 body parts contribute to how a person produces speech and each of those parts is unique to them. Voice biometric systems work by extracting the characteristics that distinguish a person’s speech from other people. The result is a “voiceprint” analogous to a fingerprint. A voiceprint is also called a “voice template.”
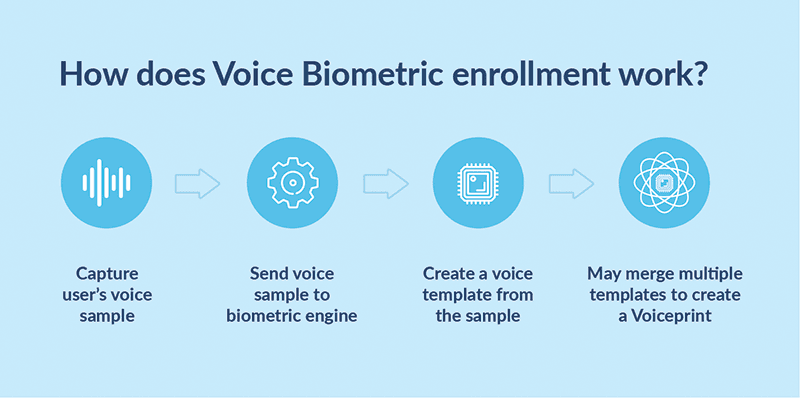
Voice recognition systems enroll a known person by creating an initial template, often merging several templates from samples of that person’s speech for higher accuracy. The initial template is called the enrollment template or enrollment voiceprint.
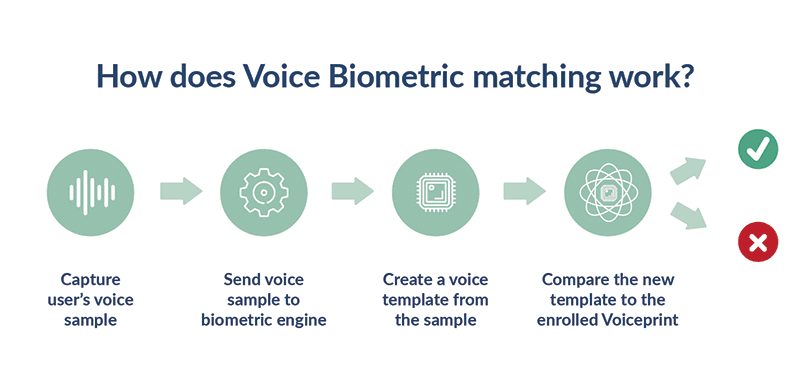
To verify an enrolled person’s identity, the biometric voice recognition system captures a new speech sample, creates a template from the sample, and compares it against the enrollment template. A strong match between templates indicates that the same person spoke both samples, thus verifying the person’s identity. This manner of using voice recognition is called Speaker Verification. It is a one-to-one match between the enrollment template and someone claiming to be the enrolled person.
Another way to use voice recognition is to compare a voice sample from an unknown identity against multiple enrollment templates. The goal is to find the person within the set of enrollment templates. This manner of using voice biometrics is called Speaker Identification. There are significant limits to accuracy for Speaker Identification, so businesses should consult with an expert to understand if a one-to-many use case with voice will be practical.
The use of voice biometrics for authentication is increasing in popularity due to improvements in accuracy, fueled largely by advances in AI, and heightened customer expectations for easy and fast access to information. Frequent password-associated data breaches are another reason for broader adoption as companies look for ways to better protect customer data.
When it comes to accuracy, it’s not just about keeping the wrong person out. Companies also have to minimize “false rejects” that cause headaches for existing customers and agents. “Equal Error Rate” (EER) s is the point where the number of false accepts and false rejects is equal. Of course the goal is to make both of these error types extremely small, ideally not allowing any impostors through with only a negligible number of valid people getting rejected.









